Do we need to renew OV/EV certificates every year after Mar-1 2020? How can Wesentra help its customers to manage the certificates in this scenario?
1.1.1970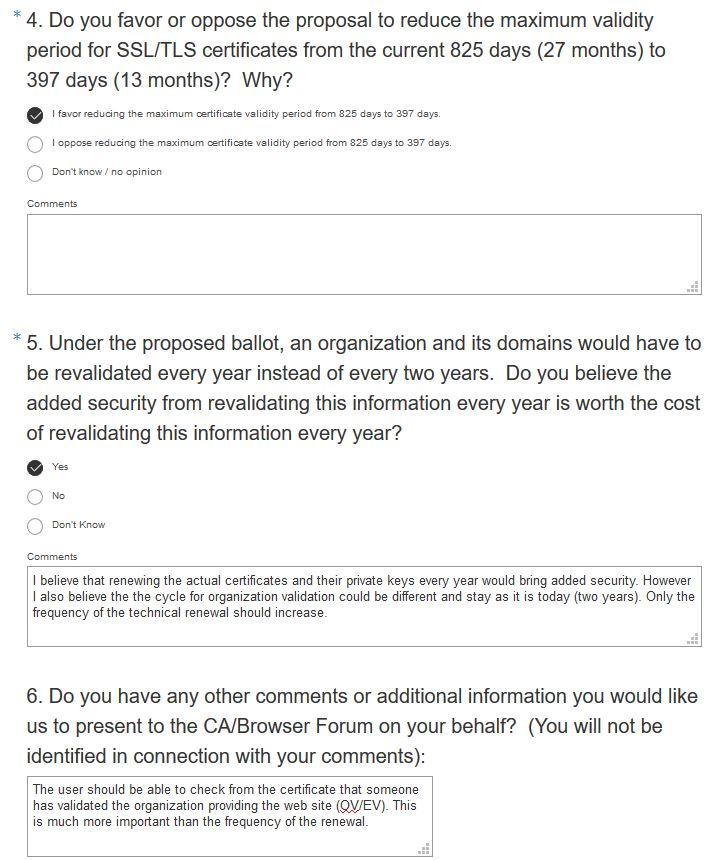
On Aug-8 2019 we learned that a browser vendor has proposed to CA/Browser Forum a ballot to reduce the maximum certificate validity to about 13 months. This change would apply to all new certificates issued on or after March 1, 2020. Now what would this mean to our customers using OV/EV certificates? My personal guess is that browser vendors force us to this and that in the future we and our partners/resellers will do a lot more of certificate managing on behalf of the customers. Partly manually and partly with still better tools/automation.
We see in the certificate world two very different development lines for giving more security to web users. With free DV (domain validated) certificates we have received encryption everywhere or at least we are approaching this goal. Let’s Encrypt certificates and their private keys are renewed automatically every 3 months. They require implementation of the method to each server but cost nothing. Unfortunately the identity of the organization providing the service cannot be checked from a DV certificate. The web site visitors are vulnerable to being on malicious web sites which are protected with legitimate DV certificates. Most sites provided by hackers have a DV certificate.
On the other hand organizations see electronic identity as the most important feature of SSL certificates (see the Forrester survey below). And here in Europe we see EU requiring certificates with strong electronic identity to its IT projects (see Chris Bailey’s presentation about eIDAS and PSD2/QWAC certificates). OV (Organization Validation) and EV (Extended Validation) certificates provide electronic identities. The web site visitor can check the organization and can be assured that a reliable third party (CA) has validated this.

My prediction is that this ballot will be accepted or that some major browser vendors will adapt this method and thus force the CAs to comply. Hopefully the ballot can be modified for example so that the cycle of organization validation would remain in two years and just the actual certificate renewal and the corresponding automatic checkout of the domain(s) would be done annually. Yes – it is useful to have new private keys for certificates every year or even every three months but the organizations change slower. For OV certificates it should be sufficient to validate the organization itself every two years.
Renewing certificates more often will increase the work for those organizations who do their own certificate renewals. A part of them will probably search to include the certificate management to their MSP contracts. And a part of them would like to outsource just the certificate management work. We need to be prepared for this.
Our partners/resellers are already now doing a lot of certificate management on behalf of their customers. As the number of certificate renewals increases we (Wesentra and our vendor Entrust Datacard) need to provide still better tools/methods for reducing the amount of work. We are already testing these methods, for example automation of certificate management via APIs and integrations to systems like ServiceNow.
I hope to see in the future a safer web with strong electronic identities and with certificates and the private keys renewed often enough. I also hope to see that the organizations don’t need to spend time for certificate management but instead the certificate providers also include to their service the needed management/automation tools.